How to Use Hardware and Software Encryption to your Advantage – Vancouver and Abbotsford BC
Hardware and software encryption are two methods of securing your data, and they each have their advantages. Here are some ways you can use them to your advantage:
- Protecting sensitive data: Both hardware and software encryption can be used to protect sensitive data, such as personal or financial information. By encrypting your data, you can prevent unauthorized access to your information, even if your device is lost or stolen.
- Complying with regulations: If you work in an industry that requires compliance with regulations such as HIPAA or GDPR, you may be required to use encryption to protect sensitive data. Using hardware and software encryption can help you comply with these regulations and avoid penalties.
- Improving performance: Hardware encryption is typically faster than software encryption, so if you need to encrypt large amounts of data quickly, using hardware encryption can improve performance.
- Adding an extra layer of security: If you’re concerned about someone accessing your data, using both hardware and software encryption can add an extra layer of security. For example, you can use hardware encryption to encrypt your device, and then use software encryption to encrypt individual files.
- Protecting your privacy: By encrypting your data, you can protect your privacy from hackers, identity thieves, and other malicious actors who may try to steal your information.
Overall, using hardware and software encryption can help you protect your sensitive data, comply with regulations, improve performance, add an extra layer of security, and protect your privacy.

Hardware Encryption Vs. Software Encryption
Keeping data files secure is an integral part of cybersecurity. It is one of the key security measures that most individuals take to prevent their files from being opened by other parties. It also keeps the contents safe from different malicious programs. An encrypted file is completely unreadable if the reader does not have the right key to the file.
Many companies invest in the best data encryption software and IT managed services to keep their data safe from outside threats. This is the most preferred solution that employees use while transferring confidential company information to other users. Data can be encrypted in various ways, although all of it uses a common mechanism. However, the best data encryption software makes sure that no decryption software employed by a hacker can open the encrypted contents unless they have the key.
How Does Encryption Work?
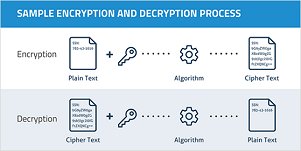
How Encryption & Decryption Process Works?
Encryption scrambles the contents of a file and makes it completely unreadable. The data used to scramble the contents is stored in a key, a randomized set of numbers, symbols, and letters. To unscramble all the gibberish, a user needs to show the same key. This key is known as the encryption key. Without it, the encrypted file is completely worthless for anyone trying to make sense of it. It is a useful technique because it flouts malicious users’ plans and saves many GB of data from falling into the wrong hands. This goes without saying that the encryption key needs to be kept safe. Attempts have been made to crack the algorithms used with the key, in an effort to re-engineer the software to allow more than one encryption key to a data set.
What is Software and Hardware Encryption?

What is Software and Hardware Encryption?
Software Encryption is the method through which users encrypt a file through the computer’s system resources. In this way, users can encrypt the file with an encryption key validated with the user’s password. This is a primary method through which any user can perform cryptographic and scrambling tasks. It does not require much processing power, and it is relatively easy to figure out with a decryption network. However, it does help perform smaller secure transfers between two users and is the most common application worldwide. It is beneficial for private networks too.
Hardware encryption, on the other hand, dedicates an entire physical processor to help the computer encrypt the file. This processor can generate a random encryption key for each file, and the user password validates the encryption key. It is much more complex and not made for amateur programmers to decrypt. This program has enormous applications in public network transfers and corporations to share confidential information. One of the good things is that it separates the encryption responsibility from the host computer’s limited resources, which helps the encryption be much more powerful.
A Comparison of Features
Both software and hardware encryption share some standard features. However, the way they provide these features is entirely different. Here, we will try to do a quick analysis of how each feature fares in both systems.
1. The longevity of the Encryption
The details of software encryption lie in the core components of the operating system. Therefore, whenever the user changes the system, they will have to switch to the latest version of the best data encryption software. This helps the user keep track of their keys and use the best version to keep their file contents secure. However, hardware encryption makes use of a separate processor which does not change properties no matter what software changes might occur. Therefore, all the data remains the same with hardware encryption, and users do not have to go through the hassle of upgrading unless specifically required to.
2. Scalability of the Encryption Program
Software encryption programs stay on the system and can be shared among multiple drives. Therefore, if a particular file from a separate drive needs scrambling, it can be quickly done. This helps a lot if users want to share the program with another device and use the best data encryption software in another file. Hardware encryption uses a physical chip that cannot be shifted to another device; that’s why users are limited to one device. In case they require the same level of encryption, they will have to buy another encryption processor for the other device. This is a pretty costly affair to engage in.
3. Dependency on the System
Software encryption depends heavily on the software. If the system itself is not secure, then the encryption key is highly compromised, and the scrambling process serves no purpose at all. On the other hand, Hardware encryption relies on a very secure processor. It does not matter how good the system is; the processor has its specifications and performance capability. It has zero dependencies on the system software and can run independently on any device. This is why hardware encryption can give the same, consistent performance for a longer period.
4. Performance of the Encryption
It is an easy guess, but software encryption relies on the computer’s processor. This single chipset has to handle both normal computer operations as well as complex encryption programming. As a result, it underperforms due to the available resources being capped. While software encryption might get bottlenecked when the computer is busy with other operations, hardware encryption consistently performs as intended with no shortfalls or inconsistencies. By utilizing the capabilities of an independent processor, hardware encryption can perform the way it is supposed to. Another point to consider is that the RAM specifications tend to play more of a critical role when it comes to software encryption. Hardware encryption isn’t nearly as affected by RAM Specifications.
Regarding Data Recovery & Its Challenge

Data Recovery Services by TSG
To recover encrypted data is very challenging. In fact, after recovering the raw sectors from a failed drive, it’s still encrypted, which means the recovered data is not readable. Encryption not only means that the information is scrambled for people with malicious interests, but its also encrypted for the user as well. In rare cases where the user loses the key, or the drive fails, the encrypted information is typically lost forever. This is a crucial point to note because users could lose access to all the data without proper precautions. Therefore, to prevent this from happening, users should consider backing up the data on other encrypted devices or cloud services.
Data Encryption is key to securing the data. However, it depends on the user which kind of encryption they want to utilize. For simple encryption problems, relying on the system’s capabilities to encrypt files is a safe choice. However, big corporations and private enterprises should not choose anything but hardware encryption to keep their confidential files private.
When we talk about Hardware encryption we mean the use of computer hardware to help or replace software with the task of data encryption. Hardware encryption is considered safer than software encryption because the process is separated from the rest. Usually, this is implemented as part of the processor’s instruction.
Here is a short list of hardware encryption devices:
- external hard drives
- self encrypting SSDs
- phones with built-in encryption capabilities
- encrypted USBs
Encrypt Your Data Professionally with TSG Data Encrypting Services
One should always seek professional assistance in case you don’t have a current backup. Our engineers at TSG managed IT services with offices in Abbotsfors and Vancouver, BC provide advice & guidance on how to recover your data and if it is at all possible to recover it or not.
Get in touch with us to get help with encrypting your private and confidential files so that your data never falls into the wrong hands. Contact us as soon as possible to get the encryption services you need.
TSG Computer Services is a Vancouver and Abbotsford based IT Support company who specializes in Security and Solutions for Increased Productivity. We have been serving the community for over 20 years. Contact us for a FREE AUDIT now to see how we can help you.
Leave feedback about this