Understanding Phishing Scams and Protecting Your Business

In today’s digital age, phishing scams are one of the most potent and widespread cyber threats. Recognizing the risks they pose is crucial for businesses like yours. Without proper knowledge, you might inadvertently fall into the trap set by these cyber adversaries through their deceptive emails.
In this article, we’ll shed light on the motivations behind phishing emails, the different techniques used by attackers, and offer guidance on fortifying your business against such threats.
What Drives Phishing Attacks?
Phishing emails are crafted with one primary purpose – to deceive. Whether it’s to trick you into parting with your money, sharing confidential data, or both, these emails often have a sinister objective:
- Financial Gains – At the heart of many phishing attacks is the desire to siphon off money. Tactics range from business email compromise (BEC) for unauthorized fund transfers to deploying ransomware to force payments.
- Stealing Valuable Data – Your business’s sensitive data, from login details to personal identification information, is a treasure trove for cybercriminals. Such data can be exploited directly or sold off in underground markets.
![]() Red Flags to Watch Out For:
Red Flags to Watch Out For:
- Emails urging you to click embedded links may be carrying malware intent on swiping your data.
- An email guiding you to an external website might lead to a malicious site designed to harvest your credentials.
- Unsolicited attachments could be laced with malicious code.
- Any email creating a sense of urgency, especially involving money transfers, warrants extra caution. Always verify the authenticity of such requests.
The Diverse World of Phishing Techniques:
- Phishing isn’t just about deceptive emails. Attackers utilize various mediums, including texts, phone calls, and even social media.
- Spear Phishing – These are tailor-made emails targeting specific individuals or organizations, often for data theft or malware distribution.
- Whaling – A subset of spear phishing, this method zeroes in on top-tier executives, impersonating trusted entities to defraud the business.
- Smishing – Smishing, or SMS phishing, uses deceptive text messages to manipulate victims into divulging information or making payments.
- Vishing – Through vishing or voice-based phishing, fraudsters pose as trusted entities, such as banks, over the phone to gather personal information.
- Business Email Compromise (BEC) – This sophisticated spear phishing variant tricks employees into making unauthorized payments, often by mimicking senior executives.
- Angler Phishing – Predominantly targeting social media users, scammers, using sham customer support profiles, deceive users into revealing personal data.
- Brand Impersonation – By impersonating renowned brands across various platforms, attackers aim to deceive customers, potentially damaging the brand’s reputation in the process.
Elevate Your Email Defenses:
While email remains a lifeline for many businesses, ensuring its security can be complex. That’s where we come in. As your trusted IT partner, we’re equipped with the tools and expertise to shield your enterprise from potential threats, allowing you to operate with peace of mind. Reach out today!
For an in-depth look at safeguarding your inbox, our eBook, “Your Guide to Email Safety”, provides practical insights and strategies. Download now!
About TSG Computer Services
TSG Computer Services is a Vancouver-based IT Support company who specializes in Security and Solutions for Increased Productivity. Contact us now to see how we can help you.
Data Loss Prevention

Let’s think for a moment that you are working away on your computer and suddenly you get an error on your screen. You think nothing of it initially, until it locks your system up. You unplug the computer like most people do, then plug it back in and turn it on. You are then presented with an error message stating that “no bootable device is present”, meaning your hard drive has just “packed it in”. You then realize that you don’t have a backup copy of anything that was on your computer!

Suddenly, your heart rate increases, and you start to panic. Your Ph.D. Dissertation, which you have worked on for months, is on that hard drive.
What would you do to get that data back? How much would you pay?
Unbeknownst to many, Hard Drive Data Recovery in Vancouver and Abbotsford BC, typically starts at $750.00 and goes as high as $5000.00. That’s right, the price of a used car.
Every Day, hundreds if not thousands of people are put in this exact situation. Their lives are put on hold as they wait for the results from the Hard Drive Recovery Labs. For some people, it’s about as stressful as waiting for the results of a medical test.
People have this misplaced trust that Hard Drives are the cure-all for lost information. Writeable CDs & DVDs typically only last up to 5 years (providing they are cared for religiously). But people don’t realize that Hard Drives are no different.
In a study performed by Carnegie Mellon University spanning 8 years, it was found when compared to the ten most common computer components to fail, that drives were rated #1. Interestingly, it was also found that SSD drives and traditional HDD drives had similar failure rates until about year 4, after which traditional HDDs failure rates rose dramatically.
1. Hard Drive 32.6%
2. Memory 17.3%
3. Power Supply 15.5%
4. Motherboard 9.6%
5. CPU 5.5%
6. Fan 5.1%
7. RAID Card 4.1%
8. Network Interface Card 2.1%
9. SCSI 1.0%
10. CD-ROM / DVD-ROM 0.6%
It was found that Hard Drives had almost 6 times the failure rate of Processors, and over 3 times the failure rate of Mainboards.
What can be done about protecting your data? A number of things really! First off, get a backup device. Whether it be a flash drive or an external Hard Drive, it doesn’t really matter. As long as your data is also stored in a secondary location. Don’t get too comfortable with Cloud Storage either. Although Cloud Storage is readily available now as a viable option, there have been plenty of instances where after a Cloud Service Update was performed, User Data went missing. Make it a habit to arm yourself with Multiple Backups of the same Data Set.

External Hard Drives currently have a much larger storage capacity than flash drives, but flash drives offer easier portability.
Next, find a backup program that takes the USER out of the equation. ie. Scheduled Daily Backups. Scheduled daily backups perform at set times each day. This removes the human element from the equation, essentially making the process more efficient.
There are a number of programs that we use to perform scheduled daily backups for our clients. These programs require no human interaction, once they are set up. They perform flawlessly, and provide that extra little bit of comfort for our clients. In addition to providing these programs, we also custom-design scripts to fit each users’ specific needs, which also back up the client’s data automatically.
If you would like to know more about how we can help your business with managed services, email us at info@tsgcs.ca
What is my business’ Cyber Security Risk?

Cyber-Security has been around for a while, but not until recently has it really gained a lot of attention. We would all hear of the odd breach here and there with respect to big companies, and thought nothing of it because 1) it wasn’t affecting us directly, and 2) we had become desensitized to it. Then came along CoVid-19, and everything changed pretty much overnight.
Companies were closing their doors, and people were being laid off. Some people were able to maintain their employment, but only by embracing the prospect of working remotely from home. For companies, this meant accepting a new normal of having employees NOT come into the office daily. With this, came challenges in Collaboration, Communication, and let’s not forget Security. Everyone was essentially thrust into the world of BYOD (Bring Your Own Device) integration.
Larger companies gave their staff, company devices to utilize at home. However, many smaller companies resorted to having their employees use their own devices for work. This presented its own set of challenges with in-house data security, and adequate security of Employees’ Personal Systems.
Now as if the whole paradigm shift to working remotely wasn’t enough, hackers saw this as an opportunity to up their game. No longer were they just going to focus on the “Bigger Fish”; they were going after the smaller companies as well. This was evident in the shear number of breaches that occurred in 2020 compared to 2019. Hackers had new targets, and they were considered easy pickings.
- These are actual, documented numbers of personal data breaches as of July 5, 2020 for years 2019 and 2020 respectively.
- 2019 (Jan 1 – Dec 31): 5.974 billion
- 2020 (Jan 1 – Jun 30): 16.092 billion
Notice that the # of breaches for the first half of 2020 exceeded all recorded breaches in 2019 by over 169%.
As Cyber Attacks grew in sheer volume, the number of data records being compromised increased exponentially. This became a big concern for Small to Medium Sized Businesses, as they were clearly in the Cyber-Criminal’s cross-hairs. Many of these same companies had/and still have no outsourced IT Support to help them navigate through these threats.
This paradigm shift in Risk Prevention promptly brought about change in the IT Industry. IT Companies made changes to their Managed Services offering, thus providing ongoing monitoring and remediation of compromised Client Information as it pertained to online data breaches.
We at TSG Computer Services in Vancouver and Abbotsford, BC have done the same. We have implemented 24/7 server monitoring of all client domains with respect to data security breaches, hardened security credentials on all our client systems, and implemented live training to deal with
What You Should Know if Your Business Is Targeted by Ransomware

It may not be news to you that ransomware is on the rise, but the numbers may leave you shocked. In 2020 alone, there were close to 300 million ransomware attacks worldwide. The cost of ransom payments demanded by hackers are also increasing in tandem with the increase in attacks. According to a recent projection, the global annual cost of ransomware attacks will touch $20 billion by the end of 2021.
Offerings like ransomware-as-a-service have made it easier for criminals with little technical knowledge to become threat actors. These attackers are less predictable and seem to lack a code of ethics. For example, groups in the past had lists of organizations they wouldn’t attack, such as cancer treatment facilities. That’s often not the case anymore.
A ransomware attack can affect any organization, regardless of size or industry. However, SMBs are the most vulnerable since cybercriminals count on these businesses to lack the resources to battle cybercrime or the IT teams to frequently evaluate cybersecurity measures. Even though SMBs continue to be disproportionately affected by these nefarious attacks, reporting and notifications rarely make the news unless a huge corporation experiences a breach.
With ransomware expected to hit businesses every 11 seconds, always remember that it isn’t a question of IF but rather WHEN your business will come under attack. Keep in mind that with the right security solutions and measures in place, your business won’t have to experience a devastating breach. But first, there are a few things you should know if you experience a ransomware attack.
Here in Vancouver and Abbotsford we are not exempt from this phenomenon. Hackers asked TransLink for $7.5 million in December.
Before Reacting to a Ransomware Attack, Remember:
1. The FBI advises against paying a ransom because spending money does not guarantee the hackers will share the keys to decrypt your data. While the FBI is an American organization, they raise a good point for businesses all across the globe.
It doesn’t make any sense to place your trust in cybercriminals who have already demonstrated that they aren’t afraid to break the law and take advantage of you for financial gain. However, many businesses find themselves in this situation because they don’t have sufficient security, backup or compliance measures, and are desperate to get their data back.
Keep in mind that another reason the FBI advises against giving in to ransomware demands is that you are encouraging criminals to conduct further attacks. If nobody ever paid ransom, it’s likely there wouldn’t be as many ransomware attacks. Criminals would have to find new ways to make money and would disregard ransomware as a viable venture.
2. In case you fall victim to a ransomware attack and have no option other than paying, “ransomware negotiators” are available for hire.
3. Victims of ransomware should expect the following:
- The data will not be erased in a trustworthy manner. It will be sold, improperly handled or stored for future extortion attempts.
- Multiple parties would have handled the exfiltrated data, making it insecure. Even if the hacker deletes a large portion of the data once the ransom is paid, other parties who had access to it may have made duplicates to make payment demands later.
- Before a victim can respond to an extortion attempt, the data may get leaked either intentionally or inadvertently.
- Even if the threat actor explicitly promises to release the encrypted data after payment, they may not keep their word.
Make Your Move Before It’s Too Late
Since no security technology or measure is flawless or guaranteed, layered security assumes that attackers will infiltrate different layers of an organization’s defenses or have already done so. The goal of this approach is to provide multiple security measures so that if an attack gets past one security tool, there are others in place to help identify and stop the attack before your data is stolen.
If the idea of protecting your business is overwhelming, don’t worry. You don’t have to do it alone. Collaborate with an experienced partner like us to do the heavy lifting for you. Our cybersecurity expertise and knowledge will help you pave the way to a more secure future. To get started, contact us for a consultation.
About TSG Computer Services
TSG Computer Services is a Vancouver-based IT Support company who specializes in Security and Solutions for Increased Productivity. Contact us now to see how we can help you.
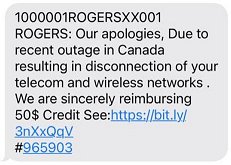
SCAM ALERT – Rogers Communications Outage Scam
I think it bears repeating, do not click on any link sent to you by text message or email from Rogers claiming to credit you for the recent Canada-Wide outage. You may not even be with Rogers – scammers don’t know this information so people on other networks still click to see if they can get money.
If and when Rogers does so, any legitimate refund will come in the form of an automatic credit on your statement. You won’t have to click on anything to receive it. Here’s an example of a fake message:
TSG Computer Services is a Vancouver and Abbotsford, BC-based computer maintenance and IT tech support firm, which prides itself on delivering effective, timely and affordable computer and IT solutions to businesses.
6 Best Computer Diagnostic Tools Listed by TSG Computer Services with offices in Abbotsford and Vancouver, BC
Please see an update to this list at the end of this article
With the advancement in technology, everything has become digital. Manual processes are being automated, the education system has embraced the use of technology, and many other major transitions have made computers an integral part of our daily work. People from all walks of life use the computer for work and entertainment alike. Computer errors thus have become a part and parcel of the digital working spaces, and that is where diagnostics and troubleshooting come into the picture. There have been advancements in manual troubleshooting, but software packages provide that extra bit of insight that make the job of troubleshooting that much easier.

Computer diagnostic tools are pieces of software that enables users to repair their own computer. These tools are either built into the operating system, available as freeware, or can be purchased from 3rd party software developers. These tools are designed to save your time and money. At TSGCS with offices in Vancouver and Abbotsford, BC, we use these tools to diagnose and resolve computer related issues.
Here are our top 6 favorite computer diagnostic tools:
1. Windows Performance Monitor
Windows Performance Monitor is an built-in tool for your Windows operating system. The performance monitor gives us a quick view of vital information linked to your computer’s hardware. This is helpful to check the CPU performance, Memory, Disk information, and Ethernet information. The Performance Monitor examines the results of running applications in both real-time and collects data for analysis and resolution later.

2. Windows Resource Monitor
Windows Resource Monitor is another reliable diagnostic tool that is more robust than Windows Performance Monitor. We employ it for tracking individual aspects of CPU, network, memory, and disk usage. It is best suited to determine what processes are affecting your CPU, how much memory is being used, what is using it, etc. The tool also diagnoses problems with TCP connections, individual process disk activity, and what processes are listening on what port.

3. Open Hardware Monitor
Open Hardware Monitor runs on Windows and Linux systems and is an open-source application.
The tool is used to monitor hardware aspects of your computer, like the temperature sensors, fan speeds, voltages, load, and clock speeds.
There are cases when the computer shuts down by itself, hangs, or crashes. The tool then can be used to diagnose if your system is overheating or the fans aren’t working properly.
It can be downloaded from https://openhardwaremonitor.org/downloads.

4. Speccy
Speccy is an all-rounder. It is a great diagnostic tool that can give you information about everything, including the software, hardware, peripherals, disk info, graphics & network data.
Speccy has an easy to use interface that makes troubleshooting and maintenance a piece of cake.
Download this tool if you are after some specific information about your computer. It will most likely have it.
Speccy can be downloaded from https://www.ccleaner.com/speccy.
5. HDDScan
HDDScan is used for HDD and SSD diagnostics. With interesting features like obtaining detailed drive info, error scanning, and determining drive health, HDDScan is a favorite tool amongst IT Professionals. Not only is HDDScan able to provide detailed info regarding HDD or SSD drives, but it also supports SCSI, USB, Firewire, and RAID drives as well. Most free programs are very limited in their ability, however HDDScan provides a host of other features like Drive Tweaks and Controls, Offline Tests, Temperature Monitoring and of course the ability to utilize a CLI. For the price tag (free), it has a lot to offer. It can be downloaded from https://hddscan.com.

6. WinDirStat
Have you ever been plagued by a computer with very little space on the hard drive? Furthermore, you dread having to spend the next hour or 3 sifting through directory after directory checking sizes manually… all in an effort to locate that elusive folder containing GigaBytes of USELESS FILES. Good news. Those days are gone. WinDirStat is your solution. WinDirStat is a “FREE” Disk Usage Statistics Viewer and Cleanup Tool for use with Windows. It works flawlessly with numerous Windows Operating Systems, from Windows XP up to and including Windows 10. I haven’t tested it yet with Windows 11. It lists folder by Size – the percentage of the parent folder being utilized. This is extremely valuable because it always shows you which folder(s) are taking up the most space. Even as you dive down into the folder structure, your eye never gets bombarded with other useless info. WinDirStat takes you right to where you are looking to go, consistently. It can be downloaded from https://windirstat.net/download.html.
In addition, there is also a MAC version of this software called Disk Inventory X, which is available at http://www.derlien.com.

The proper Computer diagnostic software package is critical when it comes to identifying and rectifying issues within a Computer System(s). These tools are designed to work automatically, with minimum effort from the end-user. They help you to isolate, discover and fix problems within your Computer System. Rather than manually searching for small, hard-to-find problems on your own, you can simply utilize the power of these software packages to help you rectify any issues found, faster.
——————
Update:
- FurMark – this is a graphics card stress testing tool that tests the stability of your GPU
- HWiNFO – this tool provides detailed information about your computer’s hardware, including the CPU, GPU, motherboard, and other components
- Malwarebytes – designed to detect and remove malware, spyware, and other malicious software from your computer
- Prime95 – this is a CPU stress testing tool that tests the stability of your CPU by putting it under maximum load
- CCleaner – scans your system for temporary files, cookies, and other unnecessary files that can slow down your computer. It also has a registry cleaner that can fix any registry issues
- CrystalDiskInfo – this tool monitors the health of your hard drive and alerts you if there are any issues. It can also provide information about your hard drive’s temperature, firmware, and other attributes
- Windows Defender – built-in antivirus program in Windows 10 that provides real-time protection against viruses, spyware, and other malicious software
- PCMark – this is a benchmarking tool that tests the performance of your computer and provides detailed results
- Memtest86 – memory diagnostic tool that checks for errors in your computer’s RAM
- Speccy – this tool provides detailed information about your computer’s hardware and software, including the operating system, CPU, RAM, and storage devices
Please contact us for a free audit.
Importance of Server Security
Servers are responsible for ensuring that the employees, management, customers, and partners have constant access to the company’s services. Server Security is a big issue nowadays. A server is at the heart of all business activities such as Data Access and Storage, Applications, File and User Control, Remote Accessibility, etc. As such, Servers are seen as a vital part of any IT environment. Unfortunately, with all this power comes an increased threat risk as well.
To mitigate this risk, a lot of companies have made the switch from in-house Servers to cloud-based solutions. Regardless of the technology your company utilizes, there are still a few basic precautions that must be continuously adhered to.

Server Security Image
Whether you employ an in-house Server or utilize cloud technology, there are still a few areas that cannot be overlooked. Network setup and security is always in the foreground of any Server utilization (whether on premise or cloud). We recommend all businesses follow these basic measures to ensure security protocols are being met.
- Ensure your Server Room is secure, and that only top level or designated personnel have physical access.
- The Server’s size should be adequate, and able to handle future company expansion.
- User access rights should be assigned with security concerns being paramount
- Install a full-suite antivirus.
- Set up an enhanced firewall.
- Ensure the Server is powered by a fully-functioning Battery Backup System
- Always Back up everything. Even in the cloud, data loss is a reality.
- Activate intrusion detection systems
- Make sure to encrypt all sensitive data
- Ensure that all software is up to date.
- Ensure the Server is monitored 24/7
What happens if a company’s server goes down?
- When a Server goes down, this is often followed by:
- Network disruption and/or failure, interruption of business processes
- Loss and/or limited access to data
- Loss of functioning applications
- Blocked access to services (for customers)
Therefore, Server optimization and Security Management are of the utmost concern. Server security protocols are designed around a comprehensive strategy that provides extensive, long-lasting protection against threats.

Server Security 2nd Image
Internet interfaces represent the most significant risk source for companies. Users should do everything in their power to secure their Network and Server. Installing antivirus software & firewalls, monitoring of suspicious traffic, etc. are some of the measures to keep the threats away. Servers themselves need to be protected from fire, humidity, power outages, break-ins, theft, and sabotage.
Measures to maintain server security
At TSG Computer Services, we provide dedicated Server Security Services designed to keep your business running. Our security measures include:
- Ensuring server room access is restricted to top-level individuals, and/or designated personnel.
- Preventative Security measures such as AntiVirus, Zero-Day Threat Prevention, Firewall and Intrusion Prevention.
- Minimizing the consequences of successful attacks
- Strong Security Policies and well-defined User Account Access profiles
Apart from securing the cloud server, servers also need to be protected from dangerous hackers who launch attacks via the Internet. Even Servers that are on the cloud, are still located in computer centers and server rooms. Equivalent to cloud protection, hardware in a server room must also be regularly maintained and checked for wear. Hardware is often exposed to a range of physical risks, such as voltage fluctuations or even earthquakes.

Server Security 3rd Image
Servers are typically set up in a dedicated room designed for centralized communications. This is where all the network traffic ends up. From here, the network traffic destined for internal departments get routed accordingly, and traffic destined for external locations gets sent to switches, routers, firewalls, and finally modems before making their way out into cyberspace.
- These Security steps need to be taken into consideration when installing server based architecture:
- Building the server room away from adjacent rooms, thereby mitigating the risks associated with water pipes and/or too much foot traffic, etc.
- Routing cables up along the ceiling, away from electrical conduits and water pipes.
- Keeping all flammable objects at a good distance from the server room.
- If setting up a server room in a big company, we ensure that the Server Room is placed on its own electrical circuit, using an isolated ground loop. This way, short circuits or tripped breakers will not have any effect on the Server Room.
- Use of emergency generators to safeguard against large-scale power outages, primarily if your servers are used for supplying services to other locations.
- Ensure systems are in place to proactively address potential problems arising from Natural Disasters
Server hardware can also get impacted by changes in temperature and humidity of the air in the room. Therefore, it is recommended that the Server Room be equipped with air conditioners, heaters, and ventilation systems. In addition, a handheld fire extinguisher is also a must-have in the server room.
Precautions to prevent attacks
Once the server is placed in its ideal location, systems are then put in place that strengthens the Server’s security from an internal and external point of view.
The simpler the system, the less error-prone it typically is. This translates into fewer software errors and loopholes that you will have to fix. Just like other systems, Servers should also be configured in such a way to be as simple and transparent as possible.
Therefore, you should only use those hardware components that are necessary for your business to function effectively. The operating system must be configured properly, and services related to the company and its purpose, and interfaces to the Internet should be kept to a minimum. If hardware components, services, or interfaces are no longer needed, then they should be uninstalled or closed. A secure server is the only way to protect a company’s data.
When it comes to the security of your Server, nothing should be left to chance. Our Advanced Threat Protection (ATP) software detects, analyzes, and prevents threats from accessing and impacting your crucial information. Let our security experts show you what a completely fortified server security solution looks like. Please contact us at TSGCS, or send an email to info@tsgcs.ca to schedule a demo.
TSG Computer Services is a Vancouver-based IT Support company who specializes in Server Security and IT Solutions for Increased Productivity. Contact us now for a free audit to see how we can help you.
Password security faux pas that users make – quick tips to help protect your passwords
How important are the doors on your home? Doors are very important. However, by themselves, they aren’t enough. Without strong locks, there is no security, and your house is always at risk. Digital property is no different.
Digital property and physical property share the same risk. Without adequate protection, your digital assets can just as easily become compromised. In this digitally progressive era, protection over digital assets has become of the highest priority. Keeping your information safe and secure is required now more than ever.
Shared passwords are often known to hackers, making it easy for them to breach the security and delve into a user’s personal details. Using easy to remember passwords, keeping the same passwords, and not implementing password change policies for all digital accounts are some of the common mistakes users make.

- Your computer password acts as the best line of defense against any threats, damaging intrusions, etc. Since passwords are commonly and widely used, users often choose a simple password that can be easily remembered. But, using a poor or common sense password can leave you vulnerable to:
- Identity theft
- Privacy invasion
- Company data exposure
- Theft of bank balance
Identity theft is currently a gold mine for cybercriminals. Imagine hackers peeping into your emails or knowing your bank login passwords; pretty risky isn’t it?
Below are the top 10 password security mistakes people make and ways to create more secure, stronger passwords.
1. Easy to Locate passwords
People often write passwords on pieces of paper or post-it notes and leave them under the keyboard. This practice screams bad password security. Passwords that can be located quickly by you can be traced by anyone else too. Password managers are an excellent option to record your password instead of writing on paper. The best passwords are those that can be remembered easily and do not have to be written down.
2. Too Common to guess
Due to the extensive use of social media, all your personal information is much more easily accessible than it was a decade ago. Birthdays, Anniversary Dates, Favorite Spots, etc. If your passwords contain any of those dates, locations, or favorite spots, you are unknowingly risking your vital data every day. Hackers have it easy when passwords consist of common phrases or patterns that are easy to guess. Even a brute force password attack can crack the password like P@55w0rd in less than 1 day. It is better to try combinations that are not so usual or are very private to you. Using everyday things as part of your password is no longer adequate.
3. Predictable password security
While creating password hints, the most commonly asked question is, “What is your mother’s maiden name?” Unbeknownst to most people, that same information is readily available on most of their social media accounts. This makes it relatively easy for a hacker to gain access to a user’s personal data, as the user would most likely enter the required name when asked for it as they would not be aware. To make the ‘coveted prize’ more difficult for hackers to acquire, try using “Ff956AKayj6Q” to answer the question of your mother’s maiden name. The trick is to keep the password hints as secret as the password. Also, try picking questions that only you can answer and whose information is not present anywhere else. This minimizes the risk of hackers.
4. Sharing passwords with your friends
Talking about security and giving away the password itself? This can be the most apparent mistake or practice that users make. Sharing passwords with friends or family is almost like sharing it with the hacker itself! When more people know your password, the risk of your password being revealed, and the chances of your account being hacked increases too.
5. Not changing passwords
Websites maintain your security in many ways. After a certain period, they prompt you to change your password so that even if hackers were close to knowing it, the risk is mitigated. Some sites do not allow users to use the same password again. A unique and strong password is the only way to ensure that your digital account is safe. Always change your password when prompted; make it a habit, and you will not be at risk.
6. Using Letters Only
Secure passwords are a combination of numbers, uppercase and lowercase letters, special characters and/or punctuation marks. Although some websites only requires the use of lowercase letters, most of them have adopted the use of both styles now. Make it a practice to use complex passwords instead of just typing in your phone number, your first name, or your last name.
7. Short in Length
It is true that shorter passwords are easier to remember, and therefore easier to type. However, that same “shorter password” is also 10x easier for a cybercriminal to crack. Websites suggest that a strong password should be at least eight characters long, contain uppercase and lowercase letters, numbers, and special characters. Some organizations are now increasing the minimum length required as well as the variety of characters to help strengthen passwords and security.
8. Creating Passwords in the Order of Password Suggestion
We often make the mistake of creating a password with the suggestions that are given to us, in the order that they are given. Although these suggestions are valuable, it is not always the best practice to use them “as is”. Mix it up a little! Instead of starting your password with a letter, start it with a number or special character. Let’s take the word “Anatomical”. Instead of using the password “Anat0mic@l”, you could write it like this. “@Nn@t0micA!”. To you and me, both passwords respresent the word “Anatomical”, but to a computer, the second password is much harder to crack. This is due not only to the abundance of special characters, but also the fact that the second variation had an extra “n”. This extra letter makes it that much harder for a computer to use a dictionary as a tool. The more complex and unorthodox your password is, the more secure it will be. This translates directly into a password that will be harder to crack.
9. Always the Same password
Using the same password for multiple websites is hands down one of the worst things that you can do. You are essentially putting all your eggs in one basket. If a cyber-criminal were to crack your password, they could potentially have access to your entire life. Although having a unique, complex password for each site you visit is a royal pain, the alternative is far worse. The biggest roadblock to creating unique, complex passwords for each site you frequent is remembering them all. We live in the digital era, and as such there are tools at your disposal which make managing passwords a breeze. Writing passwords down on a piece of paper or in an excel spreadsheet is a huge security issue. Paper can easily get misplaced, or stolen; and excel spreadsheets were never designed to hold sensitive information securely. The only way to truly be in charge of your passwords is to utilize a password manager. Password managers retain all your passwords and related information behind one encrypted door. You have one set of credentials to remember, and that’s it. Combine that with 2FA (2 Factor Authentication), and you have a door that is harder to crack. Some good password managers are: RoboForm, Keeper, Lastpass.
10. Not keeping a 2-factor authentication
Almost all websites offer a 2-factor authentication where the second security layer is connected to your phone or email to confirm that you are, in fact, the owner of the account. Two-factor authentication (2FA) implies that even if the intruders got your password somehow, they could not log in to your account until the access is confirmed by your phone. Where in reality, it is merely a deterrent. Both 2FA (2 Factor Authentication) and MFA (Multi-Factor Authentication) are hackable. In fact, no level of authentication, whether it be 2-factor, 5-factor or 7-factor is completely 100% unhackable. The only difference is, the more factors of authentication you employ, the longer it will take a hacker to compromise.
By all means, use 2FA as a starting point for your security, but if MFA is available, use that instead.

Exposure to the digital world poses risks when dealing with the threat of compromised personal information. To protect yourself and all your Personally Identifiable Information such as bank records, medical records, emails etc., you must avoid making these mistakes. Stronger cyber-smart habits are critical to the integrity of your online identity. Make each of your passwords strong and unique. Your house and car have different keys. Make sure your passwords are different as well.
Here are some quick tips to help protect your passwords:
- Use a unique password for each account.
- Use a mix of upper and lowercase letters, numbers, and symbols.
- Avoid using common words or phrases as your password.
- Use a password manager to generate and store strong passwords.
- Enable two-factor authentication for an extra layer of security.
- Avoid sharing your passwords with others.
- Change your passwords regularly, especially after a data breach or suspected compromise.
- Use a secure internet connection when accessing sensitive accounts or entering passwords.
- Be cautious of phishing scams and only enter your password on trusted websites.
- Consider using a passphrase instead of a password for added security.
TSG Computer Services is an Abbotsford and Vancouver-based IT Support company who specializes in Security and Solutions for Increased Productivity. Contact us now for a FREE audit to see how we can help you.
Malware attacks are evolving; Evolve Your Protection
Enterprises in the present world are falling prey to hackers more often than before; making malware protection a critical element for business’ success.
There is more news of businesses going down due to faulty malware protection than before. Viruses, Trojans, phishing and spear-phishing attacks, and email security threats are among the significant risks confronting organizations today. Email-borne threats are responsible for more than 90% of hacking attacks. Malware protection thus becomes the primary focus for any industry to keep their data secure and their businesses up and running.

We, at TSGCS, provide the right solution for malware protection that is easy to use and affordable at the same time. We aim to stop 100% of all threats before they reach the network.
Why do you need to evolve your protection?
Are you finding that despite using the best malware protection available, your network is still un-secure? Now is the time to arm your organization with the ability to proactively avoid malware infection.
These are signs that you should improve security standards:
- You are struggling to keep your organization free of cyberattacks using a host of endpoint security tools that require constant upgrading.
- Your malware protection is forcing you to use emergency utilities to protect your systems from the upcoming malware threats. There should have been updates from your anti-malware manufacturer to catch up with the latest malware, but this is not the case.
- You are doing your best to provide adequate threat protection for your business, but it seems like you are always one step behind when it comes to your systems’ security.
Malware protection services from TSGCS are practical. They have evolved to spot suspicious agents and protect your system from any damage, even if the endpoint does not connect to the network. In fact, every single piece of software is subject to the same Zero Trust Policy. Unless it is given a green light, it doesn’t pass… period.

Enhanced protection for better security
- Our
- empower your organizations with the following features:
- Comprehensive: be it a malicious script, a suspicious external device, or a clever file-less attack; we ensure that hackers find it very difficult to make an end-run around your malware protection system.
- Lightweight: malware protection software is designed in such a way that it can be accessed through all endpoints. We provide lightweight threat protection that requires minimal system resources to run.
- Adaptable: Our solutions use machine-learning models that effectively block any kind of unknown malware and ransomware across Windows, Mac, and Linux.
- Supported: We work with dedication to protect your system at any level. Our support personel are always ready should you need remote assistance or simply just need a question answered. Our team is all set to reply to all your requests at the earliest opportunity.

Enhanced protection for better security
When it comes to the best anti-malware systems, we prefer the multi-layered approach of using network systems to shield against all incoming threats. As more points of entry for malware become available, more shields are used to guard those entry points. Advanced threat protection uses multiple layers of protection through a secure gateway that includes DNS, URL, online, and offline payload analysis.
Advanced protection levels prevent the network from interacting with detected malware. It performs most of its rectification in a cloud sandbox. This is far more secure than a regular antivirus because it directs all network traffic to an optimal security layer via proxy chains. This approach prevents malware from delivering its payload by stopping the malware before it even gets to the network. Not only does this stop malware, but it also prevents spyware. This is achieved by blocking the malicious domains and HTTP/S URLs, and scanning all HTTP and HTTPS payloads online or offline with regularly updated malware-detection engines.

What is evolution all about?
Until today, antivirus tools had been using a signature-based solution that was successful in allowing these programs to identify external agents and eliminate them.
But now, malware and ransomware are mutating day by day or even quicker and the classic approaches are no longer adequate. Maintaining system security and promoting maximum productivity requires tools that are capable of examining each file and determining whether it is safe to run. All of this needs to be done quickly so that the end-user doesn’t experience any performance lag.
The best antimalware solutions utilize the latest technology and behavioral analysis capabilities so that the system becomes efficient to quickly examine each executable file or script and reliably make the correct run/no-run determination. All of this without the need to continually update a signature file is the advancement and evolution of malware protection software.
Our software implements application and script control, device enforcement, root cause analysis, and Automated Threat Detection and response. This is the kind of evolution that enterprise organizations need. They need to replace the current, out-dated threat protection solutions with more up-to-date solutions that will ensure the organization is fully protected from every angle, and that no possible threat avenue is left uncovered.
When it comes to the security of your business, nothing should be left to chance. Our Advanced Threat Protection (ATP) software detects, analyzes, and prevents threats from accessing and impacting your crucial information. Let our security experts show you what a completely fortified security solution looks like and how it can prevent any piece of malware from ever running on your system(s) again. Please contact us at TSGCS, or send an email to info@tsgcs.ca to schedule a demo.
TSG Computer Services is a Vancouver and Abbotsford based IT Support company who specializes in Security and Solutions for Increased Productivity. Contact us now to see how we can help you.
Testimonial 13
"From the day we hired TSG Computer Services to look after our IT services, we have been very pleased with the services they have provided to us. Chad and his staff are very professional, knowledgeable, and always there to help even during the weekends and off-hours. I would highly recommend them."
– Ranil Waliwitiya, CEO & Founder, Active AgriScience Inc.